Team up
for digital change
We provide comprehensive business consultancy and tailored IT solutions. We pride ourselves on a no-nonsense and people-first approach.




Team up
for digital change

The future is built on collaboration
Let’s create success, together.


Digital transformation for innovative companies
Bridging the gap between ambition and results
Our consultants are more than just digital specialists; they are strategists who understand your business from every angle.
We combine proven digital expertise with human-centered methods to successfully guide your business into the digital future. Our motto? Driving transformation, faster, better.
Experts in complex integration challenges
A practical integration platform promotes seamless data exchange, better client and employee experiences, and always-on access to crucial business information.
Our integration specialists make your IT landscape future-proof and ready for the artificial Intelligence revolution.
Your own application landscape of smart and fast apps
Standard packages are excellent, but sometimes they fall short. We build tailormade applications that fit your unique demands exactly.
With OutSystems, we build a customized application landscape for your ambition. Low code, high performance: applications your team loves to use and that deliver a clear return on investment.
Personalised communication tailored to your customers
No two clients are alike. Some prefer physical mail, while others rely entirely on app or email updates.
With CustomerConnect we offer a digital tool to take care of personalised communication that feels unique to every customer, whether delivered through the letterbox or digital channels.
We measure success by the positive change we create
Let's build success stories, together.

Trusted by










Our insights
All articles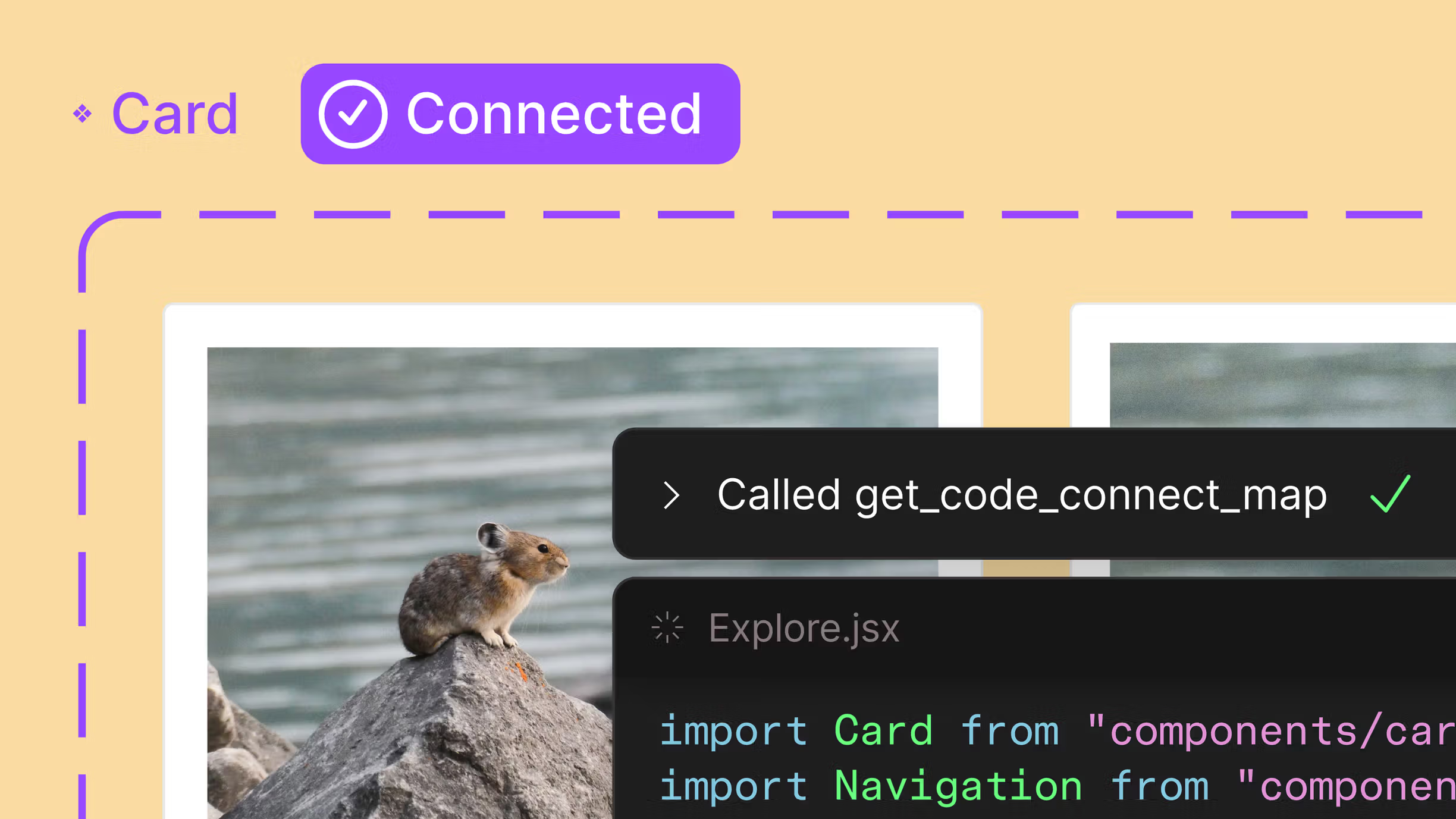
App design and development has always looked a bit like this: designers hand off mockups. Developers ask questions. Back-and-forth happens. A confused state here, wrong spacing there. More back-and-forth. Delays follow.
At Harmony IT, we’ve spent years perfecting the journey from a spark of an idea to a fully functional application. The bottleneck was rarely the code itself, more often it's the clarity between design intent and development execution.
So we asked: what if designers and developers worked together during design, not after? That simple question changed how we use Figma. It's the tool we work in before anyone opens OutSystems. We have designers and developers in the same Figma files from day one. Developers see exactly what designers intended, in real time, with Dev Mode enabled. The result? We catch misunderstandings early. We reduce back-and-forth. We ship faster and with fewer bugs.
Figma’s Three Competitive Advantages
- Real-Time collaboration
Unlike Sketch or Adobe XD, Figma is browser-native. This means stakeholders join with zero setup: no downloads, no plugins, no wait times. For organisations with distributed teams, this is transformational. We’ve seen design review cycles drop from 5 days to 2 days purely because participation improves.
- Scalable design systems
Our applications require consistency across hundreds of screens. Figma’s design system capabilities (shared components and variable documentation) mean changes propagate instantly. When you update a button style for brand compliance or accessibility standards, doing it once in Figma updates it everywhere. For OutSystems developers, this eliminates guesswork.
- Handoff
Figma’s Dev Mode serves up CSS classes and styling details directly to developers. These styles transfer nearly one-to-one into OutSystems, cutting build time and reducing bugs born from miscommunication. In our projects, Dev Mode reduces handoff friction by roughly 25–30%.
What about AI? Figma Make vs. Figma Design
No idea when you're reading this, but for now the market is genuinely changing. Tools like Framer are investing heavily in prompt-driven UI generation. You can describe what you want, and the tool builds it. Figma’s response is Figma Make, an AI feature that generates interface concepts from descriptions.
This is the era of "vibe coding": working from a clarity of purpose and letting the tool accelerate the first version.
- Figma Make supports exploration: You describe the intent, the AI generates options, and you pick a direction. It’s about capturing the "vibe" and intent without getting bogged down in pixels too early.
- Figma Design supports consolidation: Once the direction is chosen, you refine layouts, apply design system rules, and ensure the precision required for a production-ready OutSystems build.
Together, they bridge the gap. Figma Make accelerates the "vibe," while Figma Design ensures the quality.
Figma reality check?
Here is our honest assessment of why we're sticking with Figma.
| Aspect | Status | Our Perspective |
|---|---|---|
| Current Fit | Strong | Figma aligns perfectly with our high-performance delivery model. |
| Design Systems | Superior | Essential for the consistency enterprise apps demand. |
| Future risk | Moderate | AI-native tools will improve, but maintainability of automated UIs remains a hurdle. |
Our Stance: continuous evaluation
Safe to say we won't be switching tomorrow, butthat doesn't mean we aren't actively evaluating the competition.
The speed of generative UI is undeniable. In 12–24 months, the conversation might be different. For now, Figma offers the balance we need: solid fundamentals plus emerging AI, without sacrificing the rigour that enterprise applications require.

De Epic Vereniging NL (meer info) heeft onlangs officieel aangekondigd dat Harmony en MuleSoft zijn gekozen als partners voor de realisatie van een gemeenschappelijk API-managementplatform. Een vooruitstevende stap waarmee invulling kan worden gegeven aan het veranderd Zorg-ICT landschap waarin we verschuiven van traditionele integraties naar een moderne, API-gestuurde architectuur.
We spreken met Ramin Basim en Rachid Boudarbala (MuleSoft/Salesforce) en Robert Daniels en Rutger Smit (Harmony IT) over deze mijlpaal en de tienjarige samenwerking die aan dit succes ten grondslag ligt.
Waarom heeft de Epic Vereniging specifiek gekozen voor MuleSoft als API-managementplatform?
Harmony: "De Epic-omgeving is het kloppend hart van het moderne ziekenhuis. Maar dat hart moet communiceren met tientallen andere systemen: lab, apotheek, radiologie, patiëntportalen en monitoring-apps... Elk ziekenhuis heeft een uniek landschap. Zonder standaardisatie bouwen organisaties steeds opnieuw koppelingen, elk met een eigen beveiligingslaag en onderhoudslast. Dat is simpelweg niet langer houdbaar."
MuleSoft: "Precies daar ligt onze kracht. MuleSoft biedt niet alleen technische connectiviteit, maar een platform waar security, governance en reusability standaard zijn ingebakken. In de VS draaien meer dan 2.000 ziekenhuizen hun Epic-omgeving op MuleSoft; zij hebben al bewezen hoe je deze complexiteit beheerst. Die ervaring en de best-practices die we daar hebben opgebouwd, vertalen we nu direct naar de Nederlandse markt en de Europese wetgeving."
Harmony: "Deze transformatie leunt op moderne standaarden zoals FHIR (Fast Healthcare Interoperability Resources). In plaats van per ziekenhuis het wiel opnieuw uit te vinden, biedt MuleSoft een herbruikbare laag. Informatie wordt één keer veilig ontsloten en is daarna direct beschikbaar voor elke innovatie. Als het Radboudumc een slimme integratie bouwt, kan het Amsterdam UMC daar direct van profiteren. Dat is de essentie van schaalbaarheid."
Hoe past MuleSoft in de bredere uitdagingen waar de zorgsector voor staat?
MuleSoft: "Met de komst van de EU AI Act en de European Health Data Space (EHDS) moet data-uitwisseling aan extreem strenge eisen voldoen. De meest ervaren architecten begrijpen inmiddels dat je die governance niet in elke uithoek van je IT-landschap handmatig moet dichttimmeren. Je hebt een platform nodig dat die veiligheid en compliance 'by design' levert. Bovendien: zonder solide datamanagement is een AI-strategie kansloos. Als je data niet op orde is, kan AI niets voor je betekenen."
Harmony: "Zeker in een krappe arbeidsmarkt is deze synergie cruciaal. Door op hetzelfde platform te werken, kunnen zorgorganisaties kennis en oplossingen delen. Dat verhoogt de productiviteit enorm, waardoor er uiteindelijk meer middelen overblijven voor de zorg aan het bed. Die filosofie passen we overigens ook al succesvol toe in de transmurale zorg met het project 'Samen Zorgen Voor Morgen'."
Deze deal is een enorme stap. Hoe is dit partnership tot stand gekomen?
MuleSoft: "Dit was zeker geen toevalstreffer. Eigenlijk is het een resultaat van een decennium aan intensieve samenwerking. We hadden samen met Harmony al een indrukwekkende voetafdruk in de Nederlandse zorg gebouwd en Harmony heeft ook bewezen de sector echt te begrijpen. Dat trackrecord was voor de Epic vereniging ook doorslaggevend."
Harmony: "We hebben de afgelopen tien jaar diepgaande kennis opgebouwd over wat de zorgsector nodig heeft. En die samenwerking met Mulesoft loopt al een decennium goed. Dat we in 2025 door MuleSoft werden erkend als Best Performing Partner, onderstreept onze gezamenlijke visie op de markt."
In hoeverre is de wereld veranderd sinds de start van jullie samenwerking?
Harmony: "Het is een wereld van verschil. In 2015 zaten we op een summit in Amsterdam met 35 man in een klein zaaltje. Vandaag trekken MuleSoft-events 2.500 bezoekers. Wij kozen destijds voor MuleSoft na een 'bake-off' tegenover de gevestigde orde. MuleSoft leverde direct tastbaar resultaat op dag één, terwijl anderen nog aan het inventariseren waren. Die focus op snelheid vormt nog steeds ons fundament."
MuleSoft: "Destijds moesten we soms nog uitleggen wat we precies deden. Nu zijn we, zeker na de overname door Salesforce, wereldtop. Maar de kernwaarde is onveranderd: snelheid en herbruikbaarheid."
Jullie verkopen geen 'koppelingen' meer, maar 'digitale transformatie'. Is dat meer dan marketingtaal?
MuleSoft: "Absoluut. De kern van het probleem is verschoven. Oude point-to-point connecties leiden onvermijdelijk tot een onbeheersbaar doolhof. Vandaag is integratie een strategische asset; het zijn de aders van de organisatie. Bedrijven zoeken productiviteit: meer bereiken met minder mensen."
Harmony: "MuleSoft is een premium product, maar door de herbruikbaarheid en de snelheid waarmee je projecten oplevert, verdien je die investering direct terug. Dat is geen prietpraat of marketing, als je het slim aanpakt is het eigenlijk pure businesslogica."
Is dit dan ook de blauwdruk voor de rest van Europa?
Harmony: "Zonder twijfel. Wat we in Nederland doen met de Epic Vereniging en Samen Zorgen Voor Morgen (SZVM) is een schoolvoorbeeld van collectieve digitalisering. We onderzoeken nu al de mogelijkheden om dit model te kopiëren naar België en de Nordics, waar regio's zoals Denemarken en Noorwegen voor exact dezelfde uitdagingen staan."
MuleSoft: "Onze samenwerking laat zien dat we niet alleen techniek faciliteren; we maken de vitale infrastructuur van de zorg klaar voor het AI-tijdperk. Dat voedt onze Europese ambities."
Wat is jullie boodschap aan zorgorganisaties die voor vergelijkbare uitdagingen staan?
Harmony: "Doe het niet alleen. De uitdagingen zijn te complex en te urgent om zelf het wiel uit te vinden. Leer van wat andere organisaties al hebben gebouwd en kies voor platforms die samenwerking faciliteren."
MuleSoft: "En wacht niet. De technologie, de standaarden en de ervaring zijn er. Of je nu met Epic werkt of een ander systeem: modern API-management is geen luxe meer, maar een voorwaarde voor toekomstbestendige zorg."

Healthcare demand is rising while workforces shrink. For Epic hospitals across Europe, seamless data exchange isn't a luxury anymore: it's essential. The Dutch "Epic Vereniging NL" (a collaborative community of Dutch hospitals using Epic, including major institutions like Amsterdam UMC, Radboudumc, and Elisabeth-TweeSteden Ziekenhuis) recently took a significant step forward by collectively choosing a modern API management platform.
The Dutch Epic community shared their approach to shifting from traditional integrations to modern APIs:
Why This Matters for Hospitals in Denmark, Norway and beyond
By standardizing on MuleSoft with Harmony as their strategic partner, Dutch Epic hospitals are accelerating their digital transformation. The collaborative approach means hospitals share API designs, security patterns, and lessons learned: when one hospital solves a challenge, others benefit.
The Challenge You're Facing
Your Epic implementation connects to numerous systems: labs, imaging centers, municipal care platforms, HR systems, financial applications, and more. Traditional point-to-point integrations are time-consuming to build, difficult to maintain, and hard to scale.
An API management platform changes this by creating:
- Reusable APIs that work across multiple applications
- Standardised security and compliance (GDPR, NIS2) built in
- Faster deployment of new connections and services
- Better visibility into your entire integration landscape
Preparing for the European Health Data Space
The European Health Data Space (EHDS) regulation, which is into force from March 2025, creates new obligations for hospitals across Europe. By 2029, hospitals must enable cross-border exchange of patient summaries and e-prescriptions. By 2031, medical images and lab results must follow.
Denmark and Norway are actively involved in the VALO project, a Nordic collaboration to harmonise EHDS implementation. A robust API management platform helps regulatory readiness for mandatory cross-border health data exchange.
The integration foundation you build today determines your ability to meet EHDS requirements tomorrow.
What Success Looks Like
After implementing a modern integration platform, hospitals experience:
- Integration projects that complete in weeks instead of months
- Clinical teams accessing data through self-service APIs
- IT specialists focusing on innovation rather than maintenance
- Faster response to new healthcare regulations and requirements
Relevant for All Epic Hospitals
Whether you're planning your Epic rollout or optimizing your current implementation, the integration foundation matters. The principles the Dutch Epic community is applying work across borders and healthcare systems.
Let's Connect
We work with Epic hospitals across Europe and understand the specific challenges in Denmark, Norway and beyond as they closely resemble the ones in the BenNeLux. Our team can share insights from the Dutch approach and discuss how these principles apply to your situation.
Interested in learning more?



.png)

.png)




.png)

.png)